Overview #
Modern DevOps practices thrive on GitOps automation, where Git is the single source of truth for both application code and deployment configurations. While Argo CD empowers teams to declaratively manage Kubernetes manifests, keeping container images up-to-date often remains a manual or CI-driven task.
Argo CD Image Updater — an add-on service that automatically tracks new container image tags in your registries (like AWS ECR) and updates your Git repository or Argo CD Application manifests accordingly.
Think of it as the bridge between your CI (build) and GitOps (deploy) worlds — every time a new image version is built and pushed, Image Updater ensures your environment stays in sync.
Some of the key benefits of using image updater:
- Continuous Deployment: Automatically promotes new images.
- GitOps-Friendly: Writes updates back to Git.
- Registry-Agnostic: Works with ECR, DockerHub, Quay.io, GCR, etc.
- Declarative Control: Fine-tune which images, tags, or strategies to track.
How does ArgoCD Image Updater work #
At its core, the Image Updater periodically scans Argo CD Applications for special annotations. These annotations instruct it which images to watch, how to update them, and where to apply updates.
Core Workflow #
- Discover: It lists Argo CD Applications via Argo CD API.
- Inspect: Reads the annotations (e.g., argocd-image-updater.argoproj.io/image-list).
- Check Registry: Connects to your registry (AWS ECR in our case) and compares current vs. latest tags.
- Decide Update: Based on the strategy (e.g., newest-build, semver, latest).
- Write Back:
- Mode 1: Writes image tag directly into the Argo CD Application spec.
- Mode 2: Commits changes to Git repo (GitOps-compliant).
- Sync: Argo CD reconciles the updated spec and redeploys.
| Mode | Description | Usecase |
|---|---|---|
| Git Write-Back | Commits new image tags into Git (write-back-method: git) | GitOps pipelines |
| Argo CD Annotation Update | Directly patches the Application manifest inside Argo CD (write-back-method: argocd) | Ephemeral or dev environments |
Note: Use write-back-method: git for production; it preserves auditability and history in Git.
Setting Up Argo CD Image Updater on EKS with ECR #
Prerequistes #
- kubernetes cluster (EKS) - v1.29+
- ECR Registry with push access from the CI system
- IAM Role / IRSA for Image Updater with ecr readonly permissions
- Argocd installed
- Github repo hosting your manifest
Deploy argocd image updater via Helm #
Add the below specific configs in your image-updater values file
serviceAccount:
create: true
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::<AWS_ACCOUNT_ID>:role/<IAM_ROLE_NAME>
name: <IAM_ROLE_NAME>
registries:
- name: ECR
api_url: https://<AWS_ACCOUNT_ID>.dkr.ecr.<AWS_REGION>.amazonaws.com
prefix: <AWS_ACCOUNT_ID>.dkr.ecr.<AWS_REGION>>.amazonaws.com
ping: yes
insecure: no
credentials: ext:/scripts/ecr_login.sh
credsexpire: 6h
authScripts:
# -- the scripts will be mounted at `/scripts`
enabled: true
scripts:
ecr_login.sh: |
#!/bin/sh
set -eu
# Redirect AWS CLI writes to a writable path
export HOME=/tmp
mkdir -p /tmp/.aws
export AWS_CONFIG_FILE=/tmp/.aws/config
export AWS_SHARED_CREDENTIALS_FILE=/tmp/.aws/credentials
export AWS_EC2_METADATA_DISABLED=true
REGION="${AWS_REGION:-ap-south-1}"
PASSWORD="$(aws --no-cli-pager ecr get-login-password --region "$REGION")"
# single line, no trailing newline:
printf 'AWS:%s' "$PASSWORD"
helm repo add argo https://argoproj.github.io/argo-helm
helm upgrade --install argocd-image-updater argo/argocd-image-updater \
-n argocd \
-f image-updater.yaml
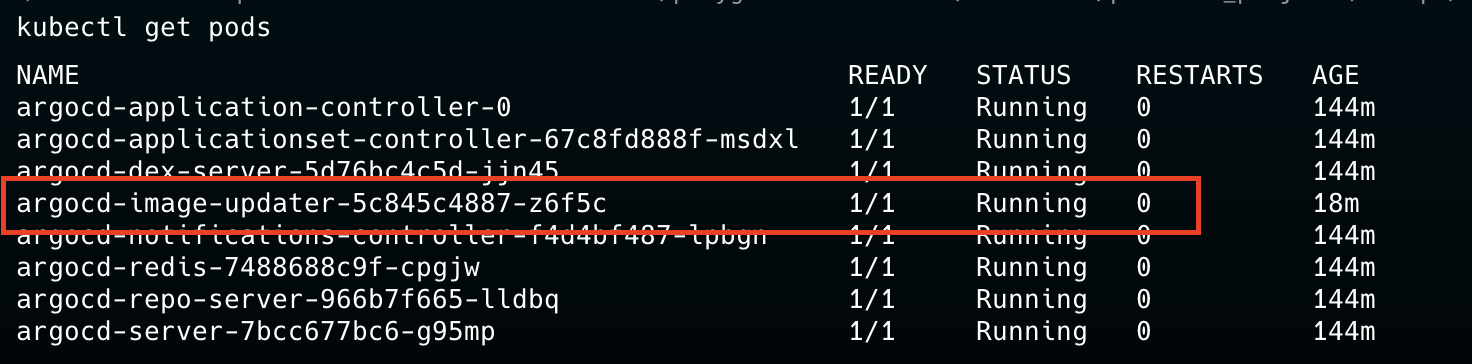
Configuring Image Updater for Argo CD Application #
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: version-service-dev
namespace: argocd
annotations:
#argocd-image-updater.argoproj.io/image-list: 720736521509.dkr.ecr.ap-south-1.amazonaws.com/codeact:~1.0
argocd-image-updater.argoproj.io/image-list: codeact=720736521509.dkr.ecr.ap-south-1.amazonaws.com/codeact:~1.0
argocd-image-updater.argoproj.io/codeact.helm.image-name: image.repository
argocd-image-updater.argoproj.io/codeact.helm.image-tag: image.tag
argocd-image-updater.argoproj.io/write-back-method: argocd
argocd-image-updater.argoproj.io/update-strategy: newest-build
spec:
project: default
source:
repoURL: https://github.com/Vinay-Venkatesh/GitOps.git
targetRevision: main
path: fastapi/charts/version-service
helm:
valueFiles:
- values.yaml
destination:
server: https://kubernetes.default.svc
namespace: version-service-dev
syncPolicy:
automated:
prune: true
selfHeal: true
syncOptions:
- CreateNamespace=true
- Image Updater monitors codeact repo in ECR.
- Whenever a new 1.x.x tag is published, it updates image.tag or directly in spec.
- Directly patches the Application manifest inside Argo CD. (write-back-method: argocd)
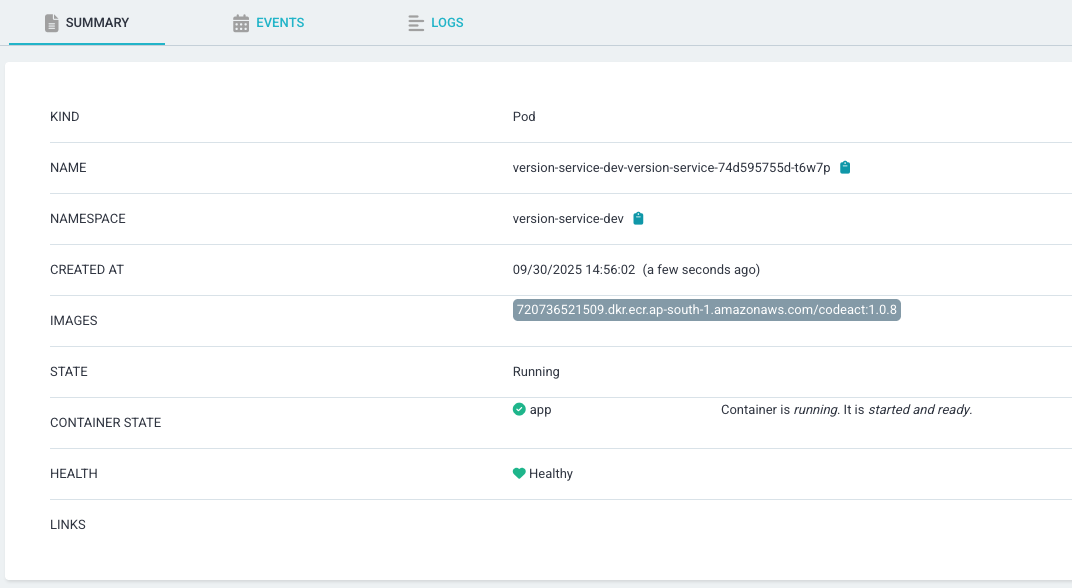
Current State:
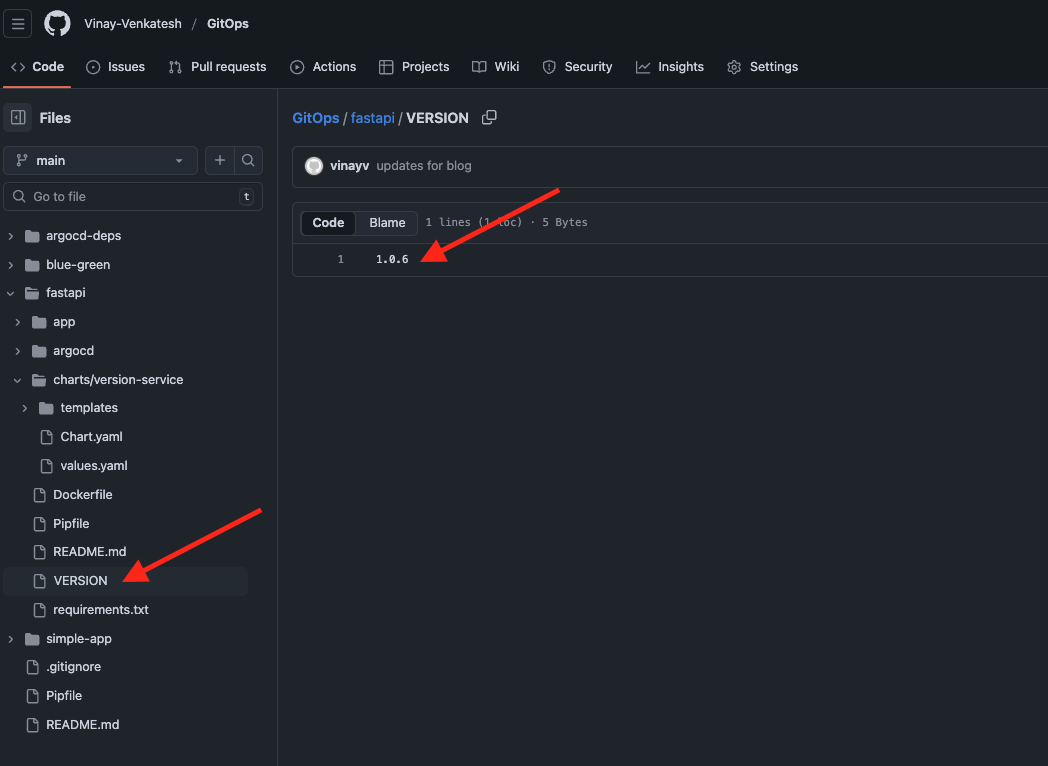
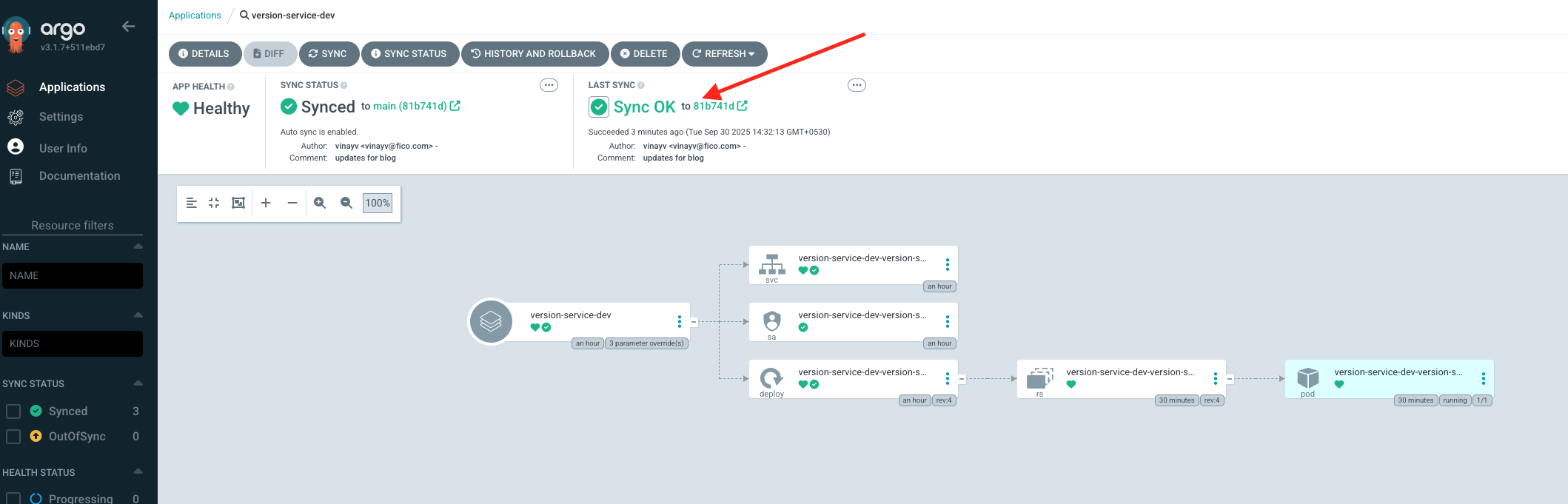
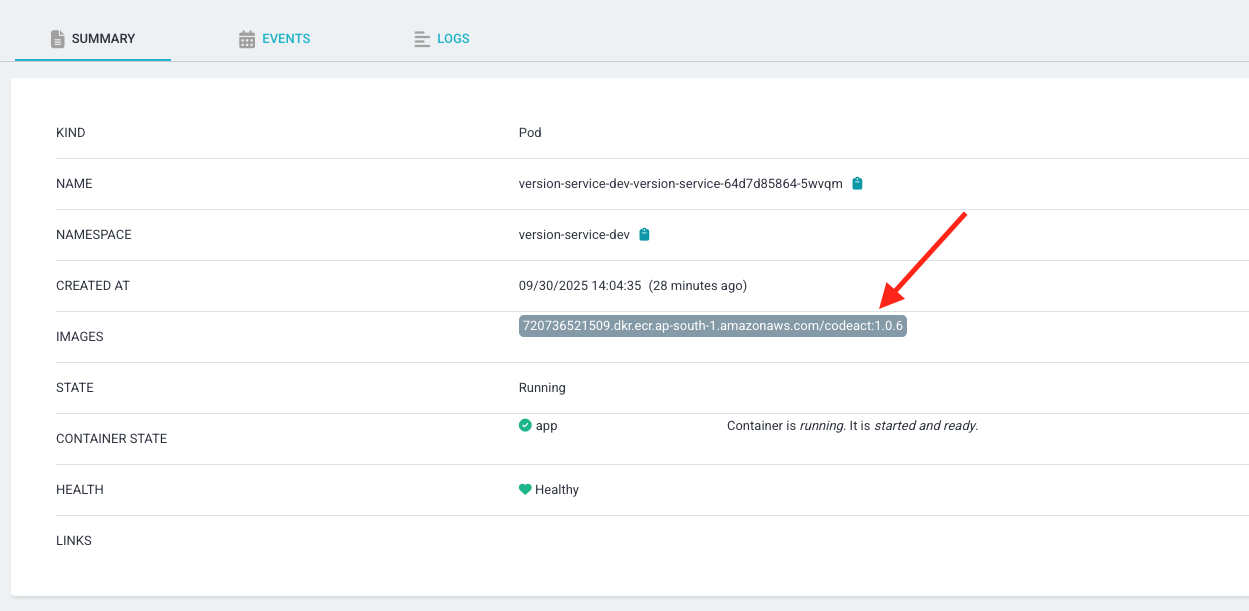
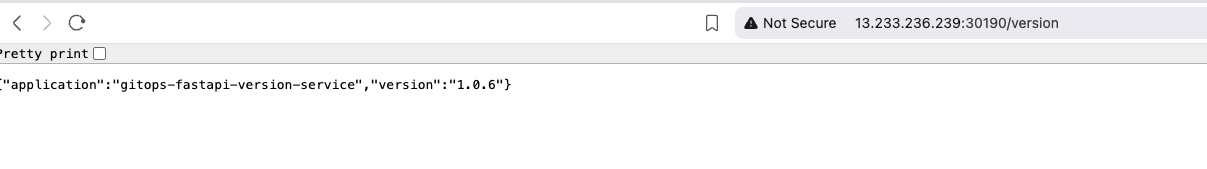
Test Argo CD Image Updater #
- First, create an image of the fastapi application and increment the tag.
- Push the new image to ECR to check if the image updater is rolling out the new image.
docker buildx build \
--platform linux/amd64,linux/arm64 \
-t 720736521509.dkr.ecr.ap-south-1.amazonaws.com/codeact:1.0.7 \
--push .
Image updater was alerted on the image push
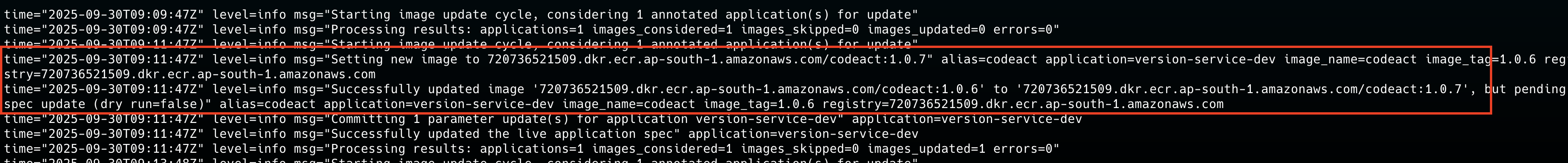
ArgoCD In place update
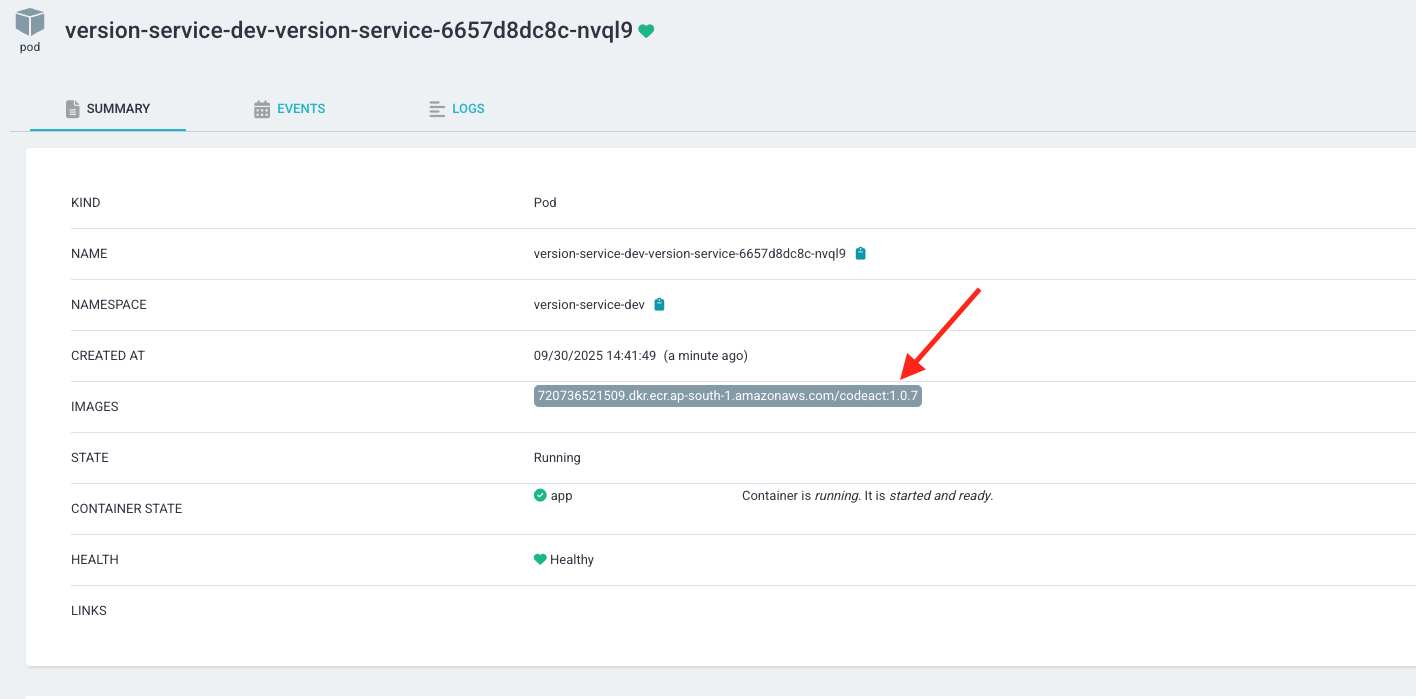
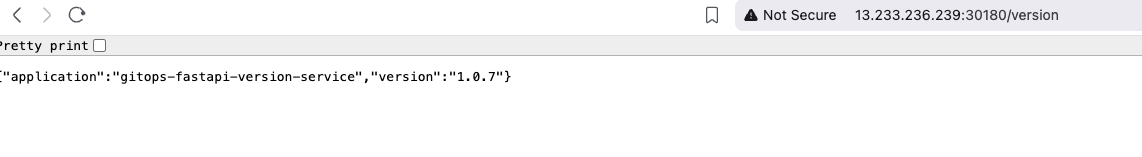
Configuring Image Updater for Argo CD ApplicationSet #
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: version-service
namespace: argocd
spec:
generators:
- list:
elements:
- name: dev
namespace: version-service-dev
valuesFile: values.yaml
template:
metadata:
name: version-service-{{name}}
annotations:
argocd-image-updater.argoproj.io/image-list: codeact=720736521509.dkr.ecr.ap-south-1.amazonaws.com/codeact:~1.0
argocd-image-updater.argoproj.io/codeact.helm.image-name: image.repository
argocd-image-updater.argoproj.io/codeact.helm.image-tag: image.tag
argocd-image-updater.argoproj.io/write-back-method: git
argocd-image-updater.argoproj.io/write-back-target: helmvalues
argocd-image-updater.argoproj.io/update-strategy: newest-build
spec:
project: default
source:
repoURL: https://github.com/Vinay-Venkatesh/GitOps.git
targetRevision: main
path: fastapi/charts/version-service
helm:
valueFiles:
- '{{valuesFile}}'
parameters:
- name: service.type
value: NodePort
- name: service.port
value: "8000"
- name: service.nodePort
value: "30190"
destination:
server: https://kubernetes.default.svc
namespace: '{{namespace}}'
syncPolicy:
automated:
prune: true
selfHeal: true
syncOptions:
- CreateNamespace=true
- Image Updater monitors codeact repo in ECR.
- Whenever a new 1.x.x tag is published, it updates image.tag and pushes the changes to git.
- Performs a git commit. (write-back-method: git)
Test Argo CD Image Updater #
- First, create an image of the fastapi application and increment the tag.
- Push the new image to ECR to check if the image updater is rolling out the new image.
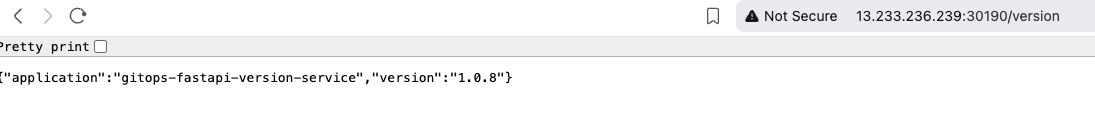
Update the version to create a new image and push it to ECR
docker buildx build \
--platform linux/amd64,linux/arm64 \
-t 720736521509.dkr.ecr.ap-south-1.amazonaws.com/codeact:1.0.8 \
--push .
Image updater was alerted on the image push
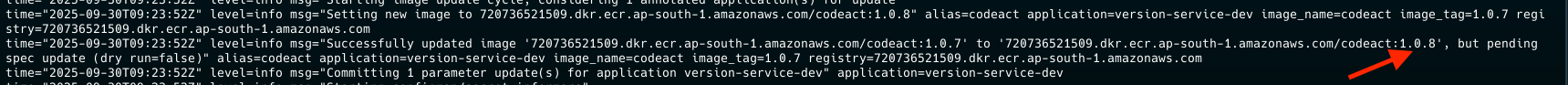
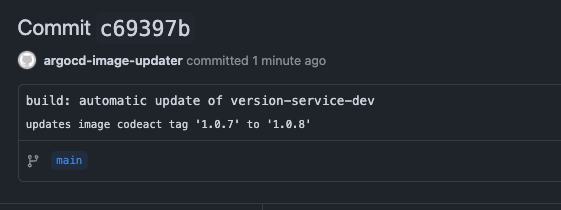
Git commit
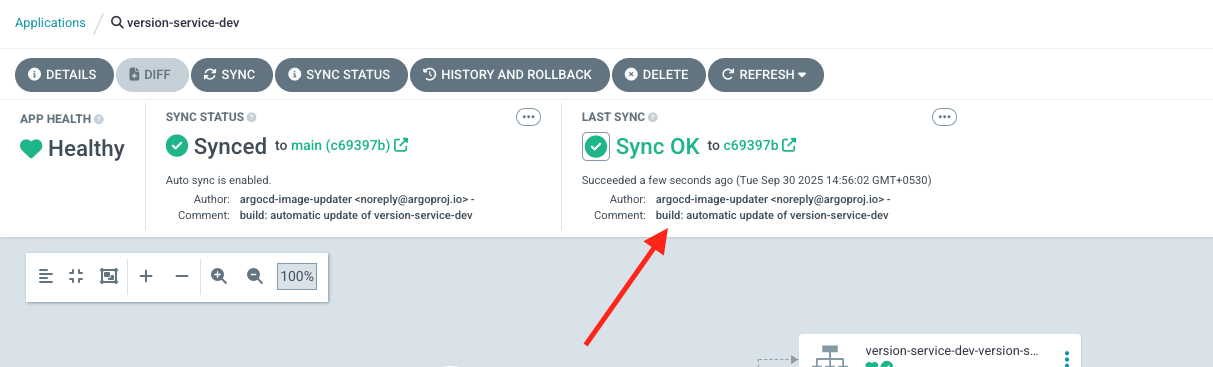
Argocd Reconciled
Summary #
By integrating Argo CD Image Updater into your EKS + ECR GitOps workflow, you achieve zero-touch image promotion — no more manual version bumps or CI scripts.
It empowers developers to focus on code, while the platform ensures continuous delivery of the latest builds in a secure, declarative, and auditable manner.
References #
- Source code - https://github.com/Vinay-Venkatesh/GitOps/tree/main/fastapi
- ArgoCD Image updater - https://argocd-image-updater.readthedocs.io/en/stable/
